
Coronavirus: Security flaws found in NHS contact-tracing app
By Megha Malhotra
Wide-ranging security flaws have been in the coronavirus contact-tracing app being piloted in the Isle of Wight. The security researchers involved have warned the problems pose risks to users’ privacy and could be abused to prevent contagion alerts being sent
GCHQ’s National Cyber Security Centre (NCSC) has acknowledged the issues, with some being already addressed and others being reviewed.
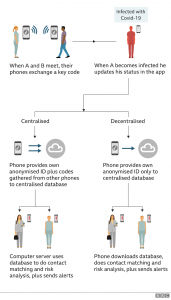
But the researchers suggest a more fundamental rethink is required. Specifically, they call for new legal protections to prevent officials using the data for purposes other than identifying those at risk of being infected, or holding on to it indefinitely. Furthermore, they recommend the NHS considers moving from its current “centralised” model – where contact-matching occurs on a PC server to a “decentralized” version – where the coordinating rather occurs on individuals’ mobiles.
“Yet there can be bugs and security vulnerabilities in either of the models,” said Cybersecurity CEO Dr Vanessa Teague. However, the huge distinction is that a decentralized arrangement wouldn’t have a central server with the ongoing face-to-face contacts of each infected individual.
“So there’s a much lower risk of that database being leaked or abused. “Health Secretary Matt Hancock said on Monday a new law “is not needed because the Data Protection Act will do the job”.
Also, NHSX, the health service’s digital innovation unit, says that using the centralised model will not only make it simpler to improve the application over time but also trigger cautions depending upon individuals’ self-diagnosed symptoms instead of simply medical test results.
Issues and risks involved
The researchers detail seven distinct issues found within the app like :
• shortcomings in the registration process that could permit attackers to sneak encryption keys, which would in turn permit them to prevent users being informed if a contact testing positive for Covid-19 and generate spoof transmissions to make logs of bogus and sham contact events.
• Gathering unencrypted Information on handsets that might potentially be utilised by law enforcement authorities to decide when at least two individuals met.
• Creating a new random ID code for users once a day instead of once every 15 minutes interval as in the case of the rival model developed by Google and Apple. The longer gap hypothetically makes it possible to determine as to whether a user is maintaining an extramarital affair with a work associate or meeting somebody after work, it is recommended.
As mentioned by Dr Chris Culnane, the second author of the report “The risks overall are varied. “Regarding the registration issues, it’s fairly low risk since it would require an attack against a well secured server, which we don’t believe is particularly likely.
“But the risk about the unencrypted data is higher, because if someone was to get access to your phone, then they might be able to learn some additional information because of what is stored on that.”
Measures taken in this direction
An NCSC spokesman said: “It was always hoped that measures such as releasing the code and explaining decisions behind the app would generate meaningful discussion with the security and privacy community. We look forward to continuing to work with security and cryptography researchers to make the app the best it can be.”
According to Dr Culnane, politicians are also needed to re-address the issue.” I have confidence that they will fix the technical issues,” he added. In any case, there are extensive issues around the Lack of legislation ensuring utilization of this information [including the fact] there’s no severe limitation as to when the information must be deleted. “That’s in contrast to Australia, which has very strict limits about deleting its app data at the end of the crisis.”
Ad interim, Harriet Harman, who’s the head of the Parliament’s Human Rights Committee, reported herself looking for authorization to acquaint a private member’s bill to limit who could utilize the information accumulated by the app and how and make a watchdog to manage related protests from general society.
Concluding with the views of the labour MP, “I would personally download the app myself, even if I’m apprehensive about what the data would be used for. But the view of my committee was that this app should not go ahead unless [the government] is willing to put in place the privacy protections.”
Sources :
Cryptography system should be used properly, symmetric cryptography be available to only to user to see related private information on his mobile as well as u.sec.5(2) of telegraph act,1885 rules be made stricter.overall article is very nice.
This article is really makes sense, after the launch of AROGYA SETU APP. People have lots of questions about this app like what is the pro and cons exactly. Whether mobile data is safe to use this app or not? This article will helpful to them.
Very informative
Very informative one article
targets major glitches in the app, we could be at high risk of data leak.
Like!! Really appreciate you sharing this blog post.Really thank you! Keep writing.
Informative article
Government now are using more apps and making use of the various resourced which are available to them to counter and check the spread of Covid-19. But in order to do so sometimes minute details are ignored.Hackers always looks for loopholes into the system in order to corrupt the system , everything online is a system of various codes and these codes may have one loophole or even many depending upon the time taken by the coder to make it. Cyber security experts use buggs or firewalls to prevent any hack into the system because it may be impossible to create a system without loopholes but the hacker can be prevented.